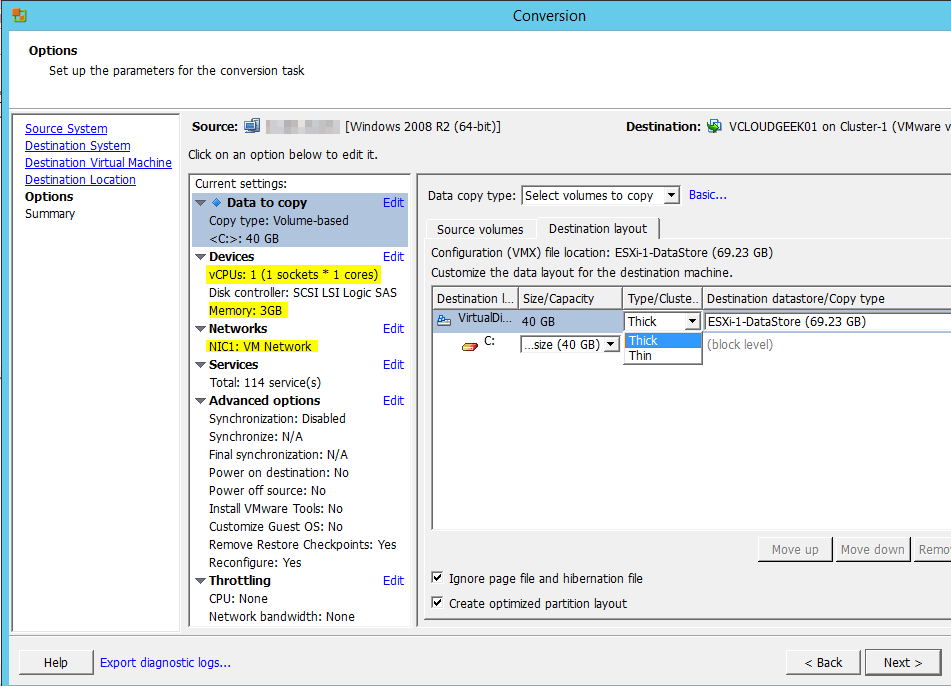
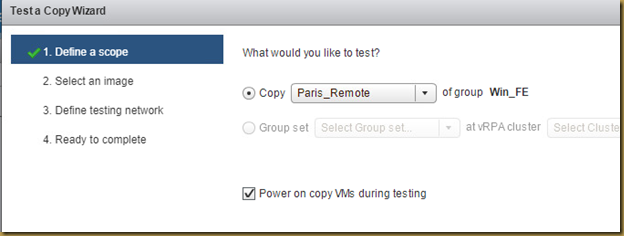
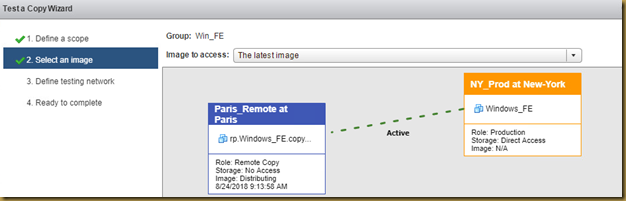
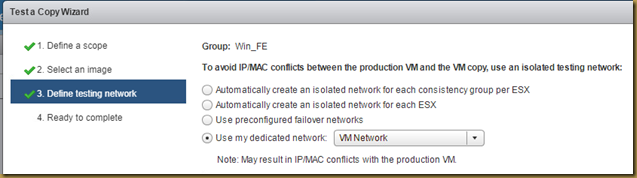
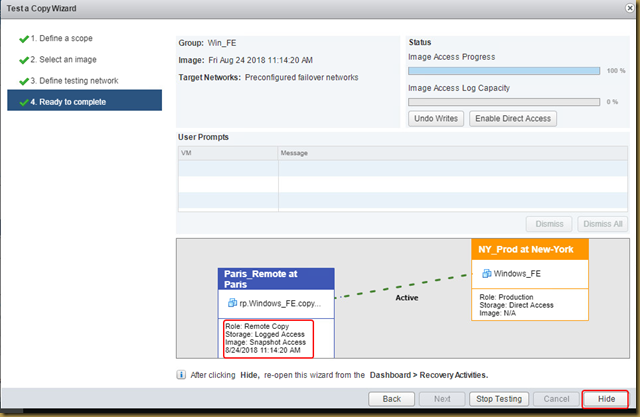
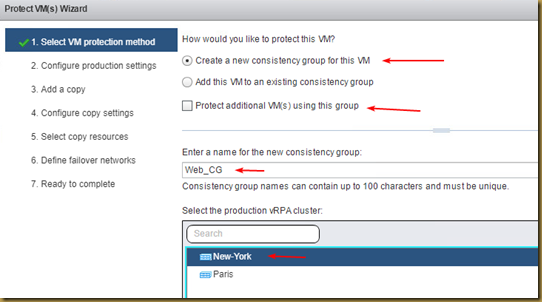
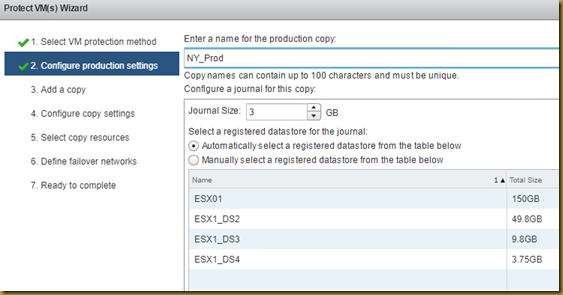
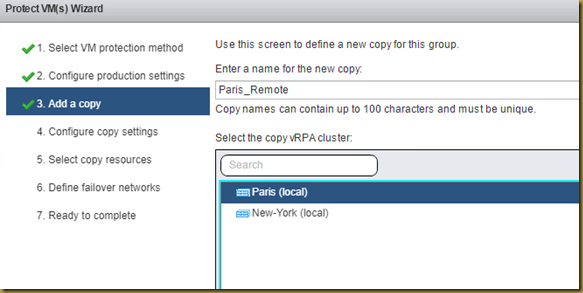
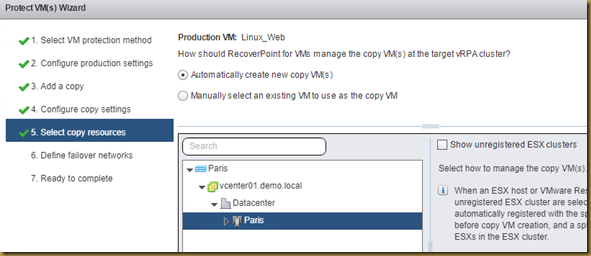
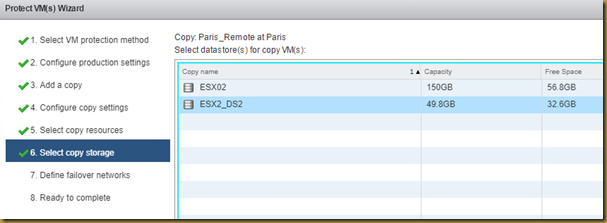
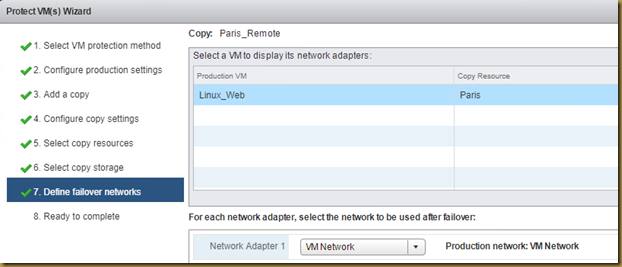
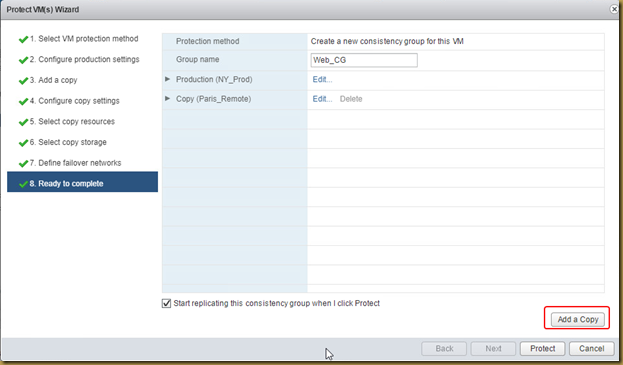
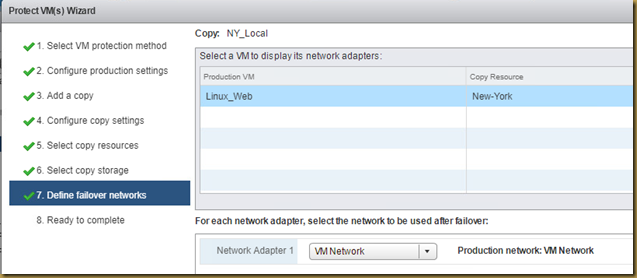
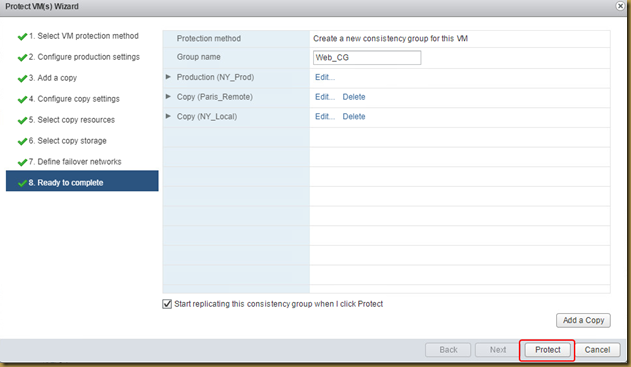
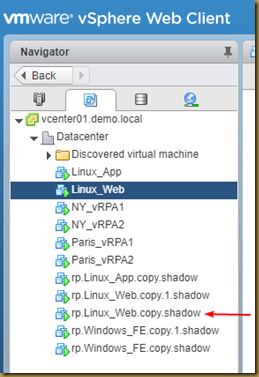
The EMC Grab Utility runs a series of host based commands and utilities that collect system information to provide to EMC Support for problem troubleshooting. It collects specific details like server configuration, installed programs, updates/patches, storage and disk information, drivers, event logs etc.
The EMC Grab report creates a zip file. The Windows version of the EMC Grab is the EMC Report.
Windows versions(x86 & x64) download link:
ftp://ftp.emc.com/pub/emcgrab/Windows/
UNIX versions (all flavors) download link:
ftp://ftp.emc.com/pub/emcgrab/Unix/
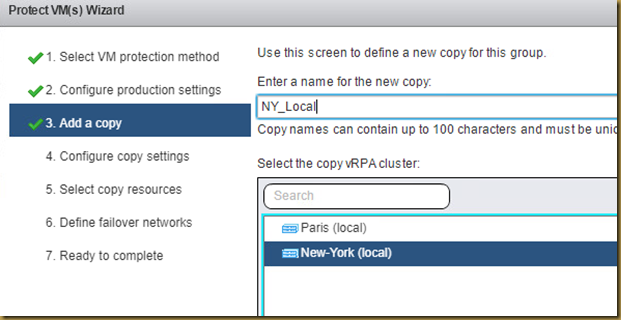
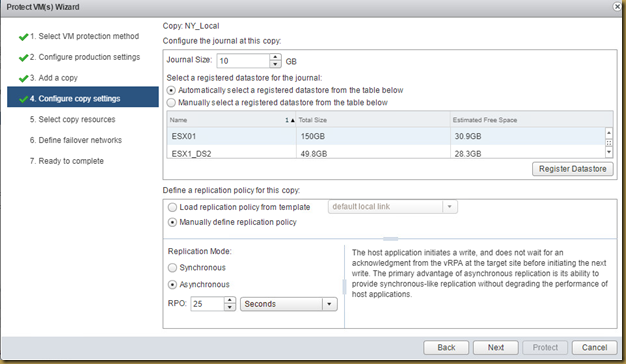
Steps to run on Windows Server:
1. Download the EMC Grab Utility as per your windows server version.
2. Double click on EMCRPTS_X64_V61.exe
3. Now you can see a command prompt screen running and collecting various system details.
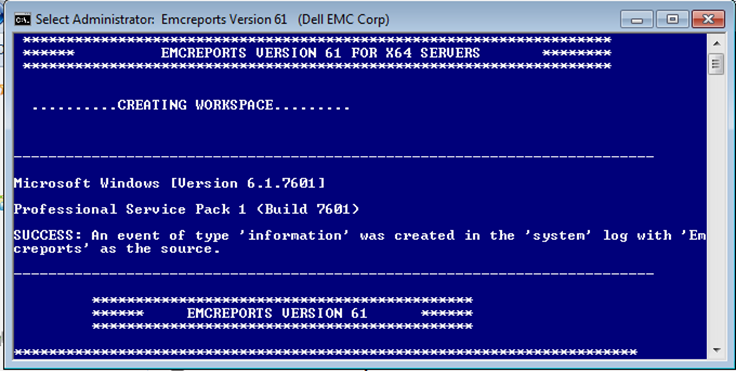
4. Once it completes the collection, the zip file will be saved in the below path:
"C:\Windows\Emcreports\COLLECTION\ZIP"
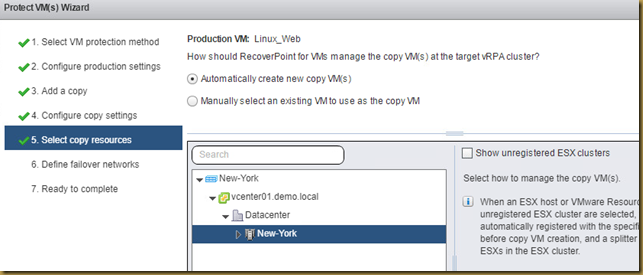
Steps to run on Linux server:
1. Download the EMC Grab Utility as per your Unix server version.
2. Copy it to the server and extract it.
3. Run the script.
DO YOU AGREE TO ACCEPT THE TERMS & CONDITIONS OF THIS LEGAL AGREEMENT (Y/N): Y
1) Please Enter Service Request Number:
2) Please Enter Customer Party Number (Site ID):
3) Please Enter Customer Company Name:
4) Please Enter Customer Contact Name:
5) Please Enter Customer Contact Phone Number:
6) Please Enter your Email Address:
Hostname / OS Info: Your_HostName / Linux
Is the EMC Grab Identification Information Correct (Y/N) : YDo you want to collect SMI-S information (y/n) ? N
Do you want to collect XtremIO Array information (y/n) ? N
Please approve that you verified that the script version is up to date (y/n)? Y
Please submit this file to EMC for Analysis. Thank you
Removing Temporary Files....
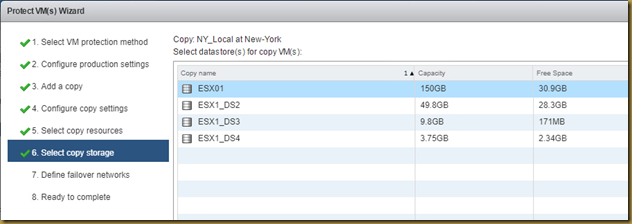
4. Verify the output file is created under /usr/emc/outputs OR your specific path you provided.
File Name: HostName_YYYY-MM-DD-HH.MM.SS_Linux_emcgrab_V4.8.1_CC0000000000.tar.gz
5. Now copy the output from the source server using SCP or other tools.
The EMC Grab report creates a zip file. The Windows version of the EMC Grab is the EMC Report.
Windows versions(x86 & x64) download link:
ftp://ftp.emc.com/pub/emcgrab/Windows/
UNIX versions (all flavors) download link:
ftp://ftp.emc.com/pub/emcgrab/Unix/
Steps to run on Windows Server:
1. Download the EMC Grab Utility as per your windows server version.
2. Double click on EMCRPTS_X64_V61.exe
3. Now you can see a command prompt screen running and collecting various system details.

4. Once it completes the collection, the zip file will be saved in the below path:
"C:\Windows\Emcreports\COLLECTION\ZIP"
Steps to run on Linux server:
1. Download the EMC Grab Utility as per your Unix server version.
2. Copy it to the server and extract it.
| root@hostname usr] # tar –xvzf emcgrab_linux_v4.8.1.tar root@hostname usr] # cd emcgrab |
3. Run the script.
| root@hostname usr] # ./emcgrab.sh |
DO YOU AGREE TO ACCEPT THE TERMS & CONDITIONS OF THIS LEGAL AGREEMENT (Y/N): Y
1) Please Enter Service Request Number:
2) Please Enter Customer Party Number (Site ID):
3) Please Enter Customer Company Name:
4) Please Enter Customer Contact Name:
5) Please Enter Customer Contact Phone Number:
6) Please Enter your Email Address:
Hostname / OS Info: Your_HostName / Linux
Is the EMC Grab Identification Information Correct (Y/N) : YDo you want to collect SMI-S information (y/n) ? N
Do you want to collect XtremIO Array information (y/n) ? N
Please approve that you verified that the script version is up to date (y/n)? Y
Please submit this file to EMC for Analysis. Thank you
Removing Temporary Files....
4. Verify the output file is created under /usr/emc/outputs OR your specific path you provided.
File Name: HostName_YYYY-MM-DD-HH.MM.SS_Linux_emcgrab_V4.8.1_CC0000000000.tar.gz
5. Now copy the output from the source server using SCP or other tools.